Home /
Expert Answers /
Computer Science /
context-configuring-context-based-access-control-cbac-and-zone-based-firewalls-figure-1-topology-pa608
(Solved): Context Configuring Context-Based Access Control (CBAC) and Zone-Based Firewalls Figure 1 Topology ...
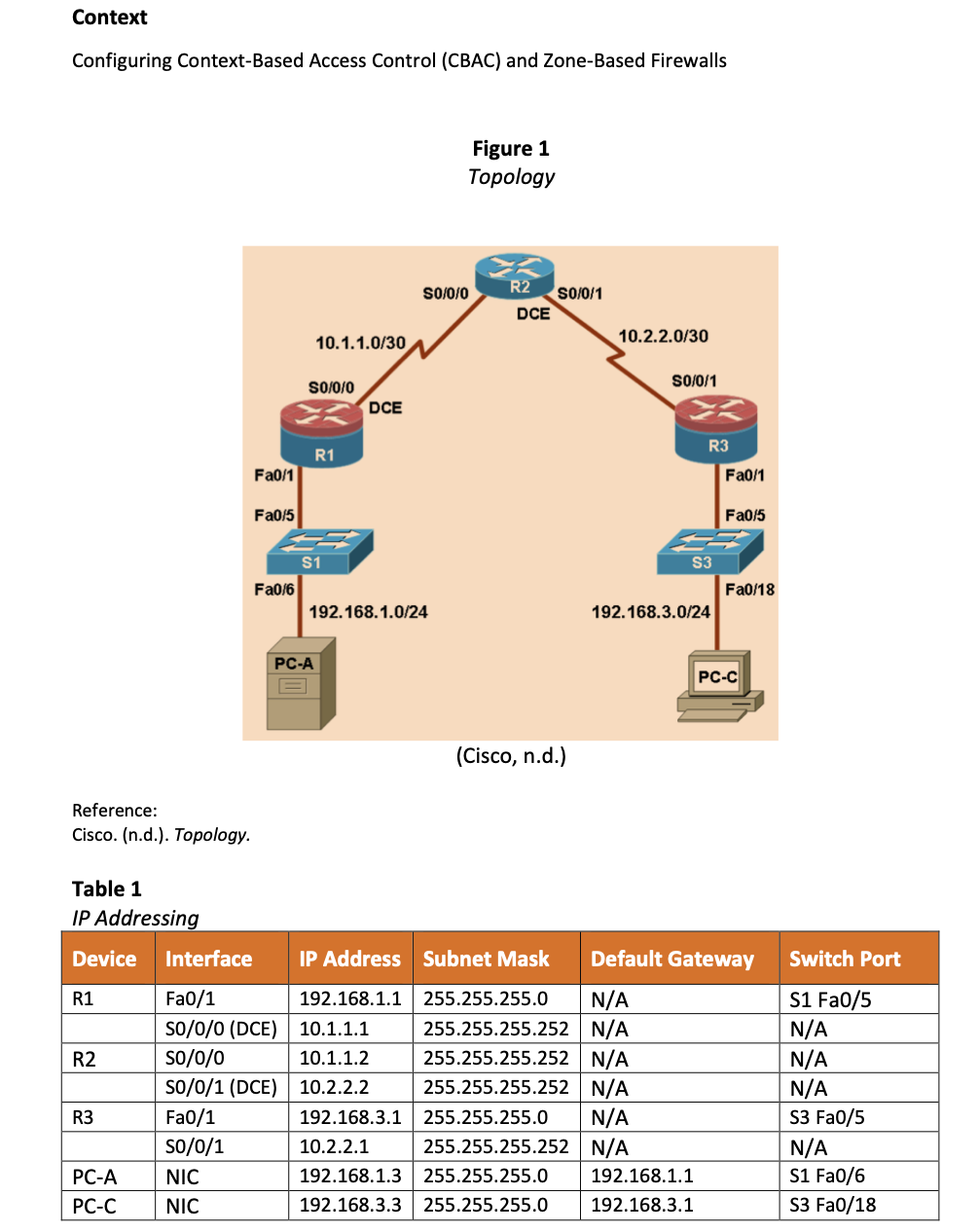
Context Configuring Context-Based Access Control (CBAC) and Zone-Based Firewalls Figure 1 Topology (Cisco, n.d.) Reference: Cisco. (n.d.). Topology. Table 1 IP Addressina
Steps to Configure CBAC and Zone-Based Firewalls Objectives Part 1: Router Configuration - Configure interface IP addresses, hostnames and access passwords. - Configure the Enhanced Interior Gateway Routing Protocol (EIGRP) routing protocol. Part 2: Configuring CBAC Firewall - Configure CBAC using AutoSecure. - Test the CBAC configuration. - Validate the firewall functionality. Part 3: Configuring a Zone-Based Policy Firewall - Utilise CCP to configure a zone-based policy firewall. - Validate CBAC configuration. - Utilise CCP Monitor to attest configuration. Resources Required - 2 switches (Cisco 2960 or comparable) - 3 routers (Cisco 1841 with Cisco IOS Release 12.4(20)T1 or comparable) - Rollover cables to configure the routers via the console - PC-A: Windows 7 - PC-C: 7 with CCP 2.5 - Serial and Ethernet cables as shown in the topology Written Report on Practical Cybersecurity Solutions Your report must follow the following structure: - A title page with the subject code and name, assignment title, your name, student number and lecturer's name - An overview that will also serve as your statement of purpose for the report-this means you are going to provide an introduction about the network solution you are proposing. You will need to inform the reader of the: ○ setup environment ○ summary of the report. - Main body. You need to provide sufficient screenshots along with an explanation under each piece of evidence and command line. - Conclusion. In this section, you are required to review all the results and outcomes of the implementation of the network solution and after validating the firewall functionality covered in the report.