Home /
Expert Answers /
Computer Science /
please-write-a-full-description-and-explanation-for-the-drawing-pa791
(Solved): Please write a full description and explanation for the drawing ...
Please write a full description and explanation for the drawing stare machine diagram
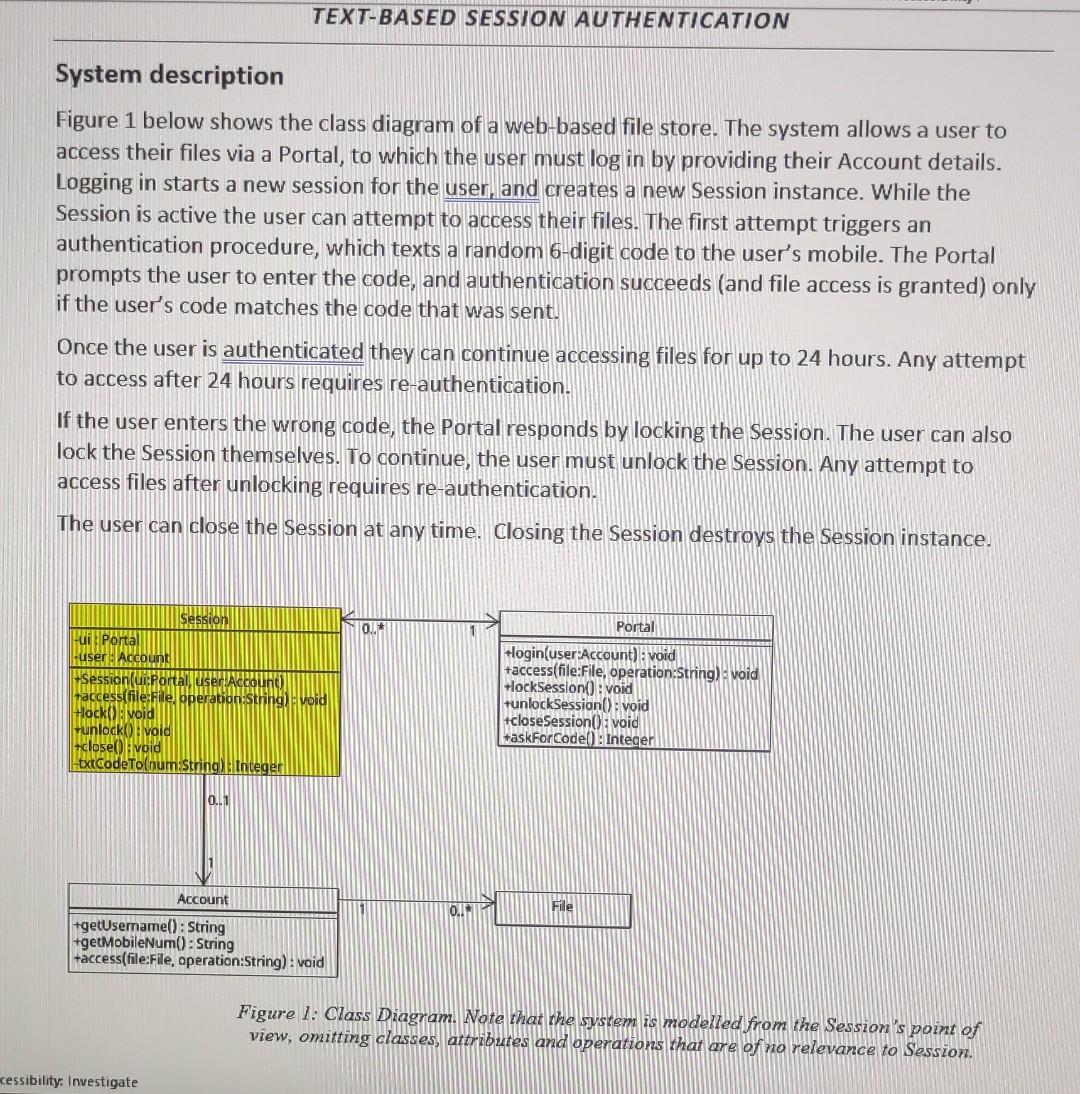
System description Figure 1 below shows the class diagram of a web-based file store. The system allows a user to access their files via a Portal, to which the user must log in by providing their Account details. Logging in starts a new session for the user, and creates a new Session instance. While the Session is active the user can attempt to access their files. The first attempt triggers an authentication procedure, which texts a random 6-digit code to the user's mobile. The Portal prompts the user to enter the code, and authentication succeeds (and file access is granted) only if the user's code matches the code that was sent. Once the user is authenticated they can continue accessing files for up to 24 hours. Any attempt to access after 24 hours requires re-authentication. If the user enters the wrong code, the Portal responds by locking the Session. The user can also lock the Session themselves. To continue, the user must unlock the Session. Any attempt to access files after unlocking requires re-authentication. The user can close the Session at any time. Closing the Session destroys the Session instance. Figure 1: Class Diagram. Note that the system is modelled from the Session's point of view, omitting classes, attributes and operations that are of no relevance to Session.
The intended behaviour of a Session instance is specified by six representative scenarios that are shown on the following pages in the form of six sequence diagrams, depicting the interactions between a Session instance and instances of the other classes in the system.
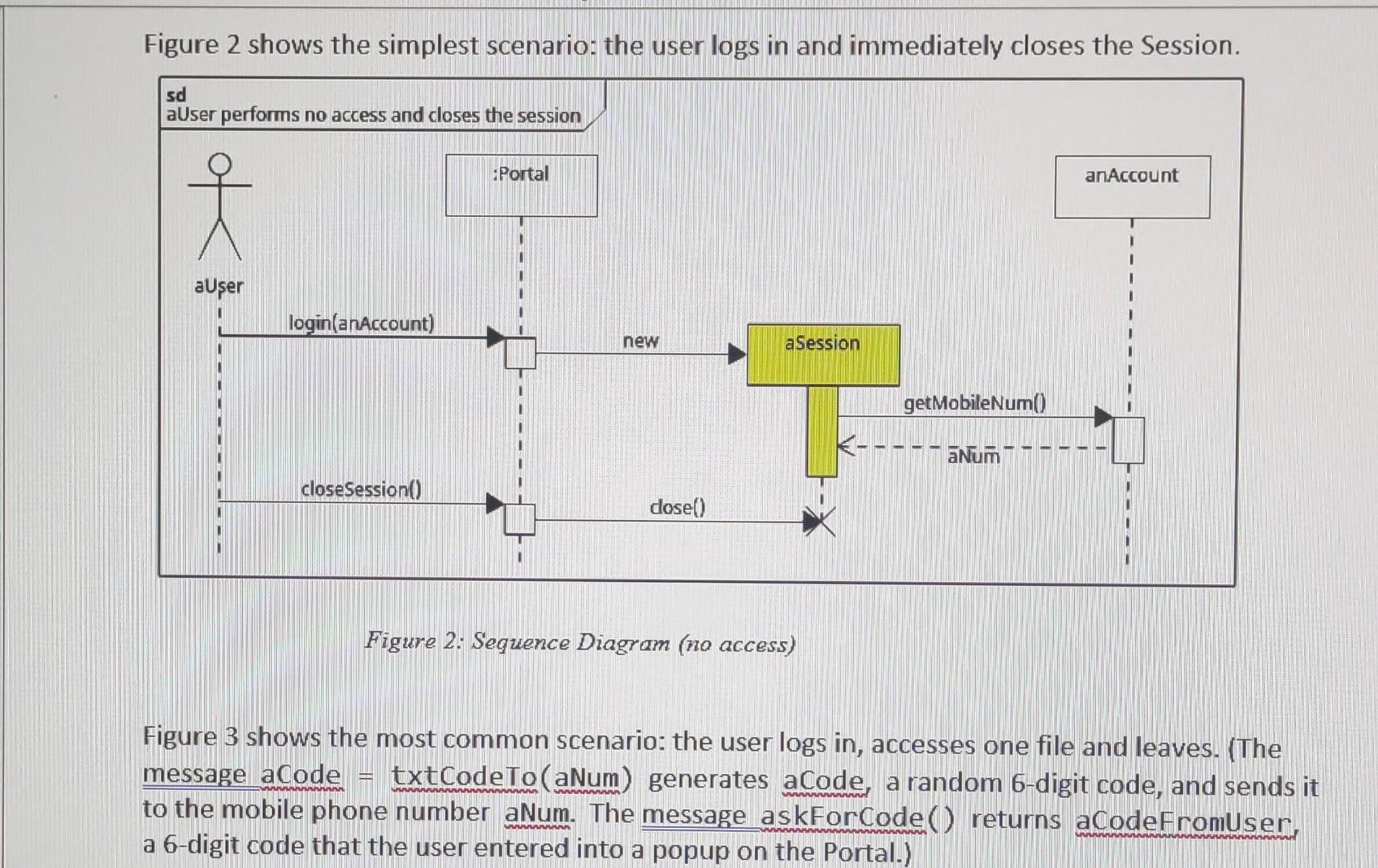
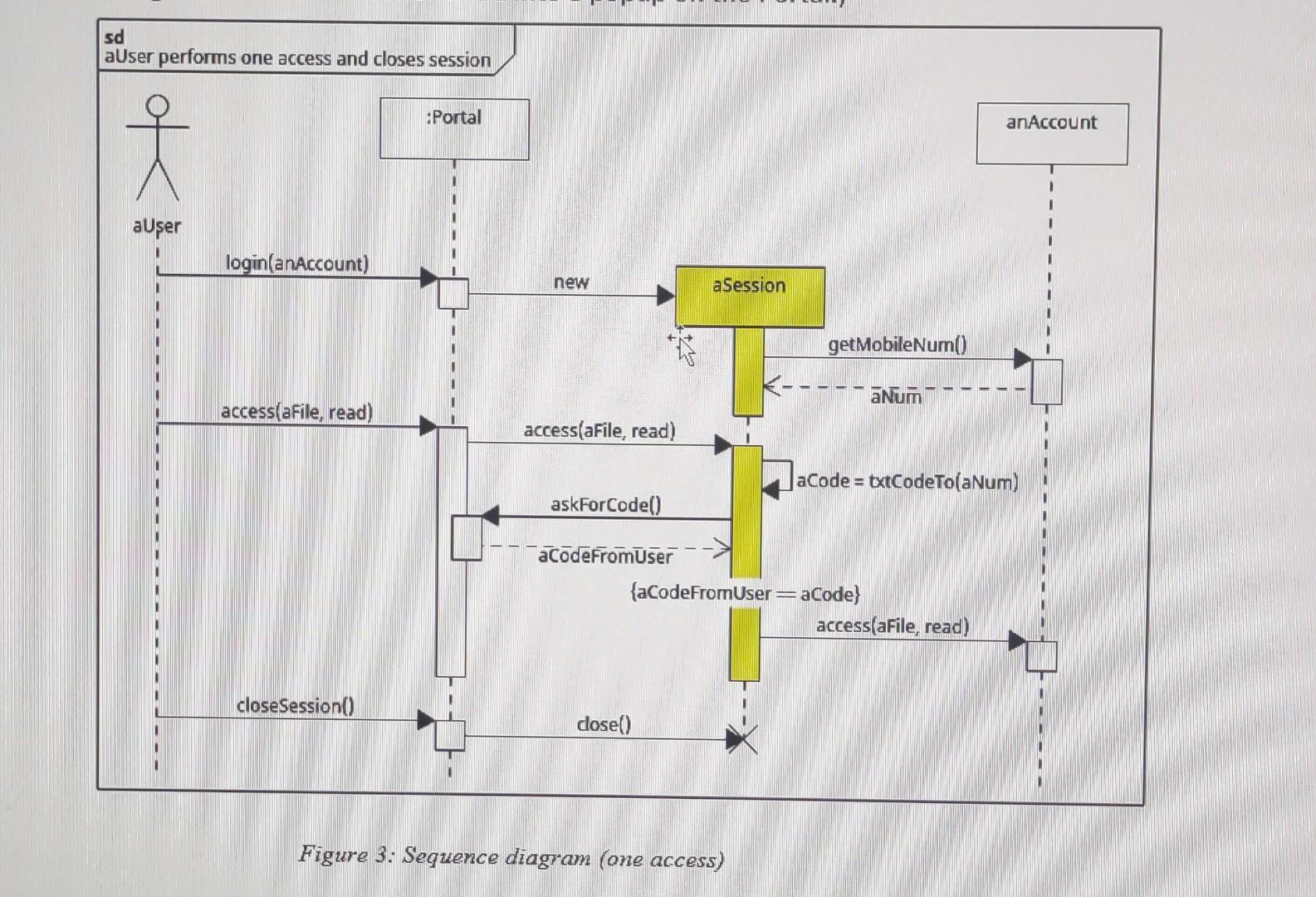
Figure 2 shows the simplest scenario: the user logs in and immediately closes the Session. Figure 2: Sequence Diagram (no access) Figure 3 shows the most common scenario: the user logs in, accesses one file and leaves. (The message aCode txtCodeTo (aNum) generates aCode, a random 6-digit code, and sends it to the mobile phone number aNum. The message askForCode () returns aCodeFromuser, a 6-digit code that the user entered into a popup on the Portal.)
Figure 3: Sequence diagram (one access)
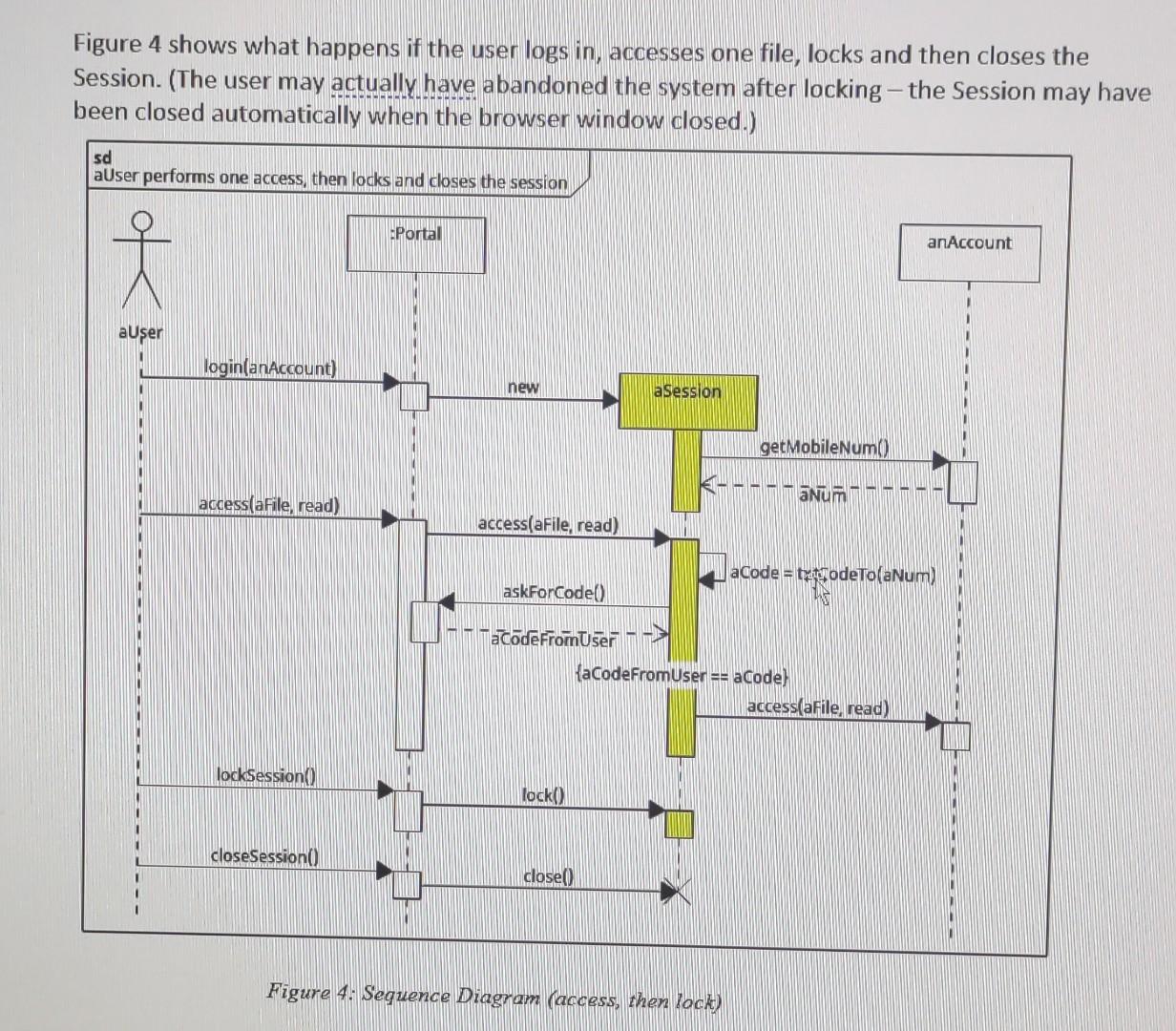
Figure 4 shows what happens if the user logs in, accesses one file, locks and then closes the Session. (The user may actually have abandoned the system after locking - the Session may have been closed automaticallv when the browser windown alncod i Figure 4: Sequence Diagram (access, then lock)
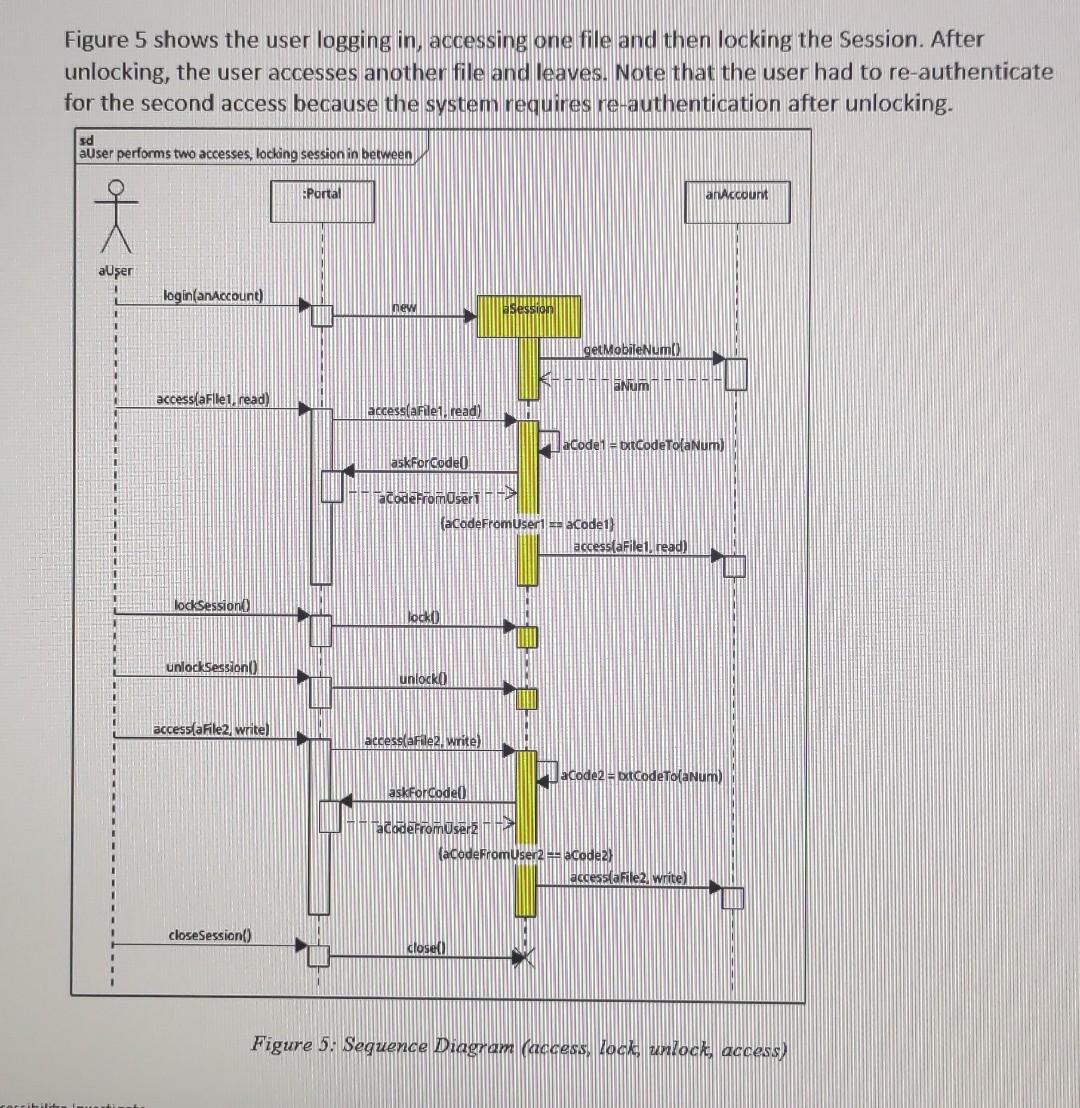
Figure 5 shows the user logging in, accessing one file and then locking the Session. After unlocking, the user accesses another file and leaves. Note that the user had to re-authenticate for fter unlocking. scid
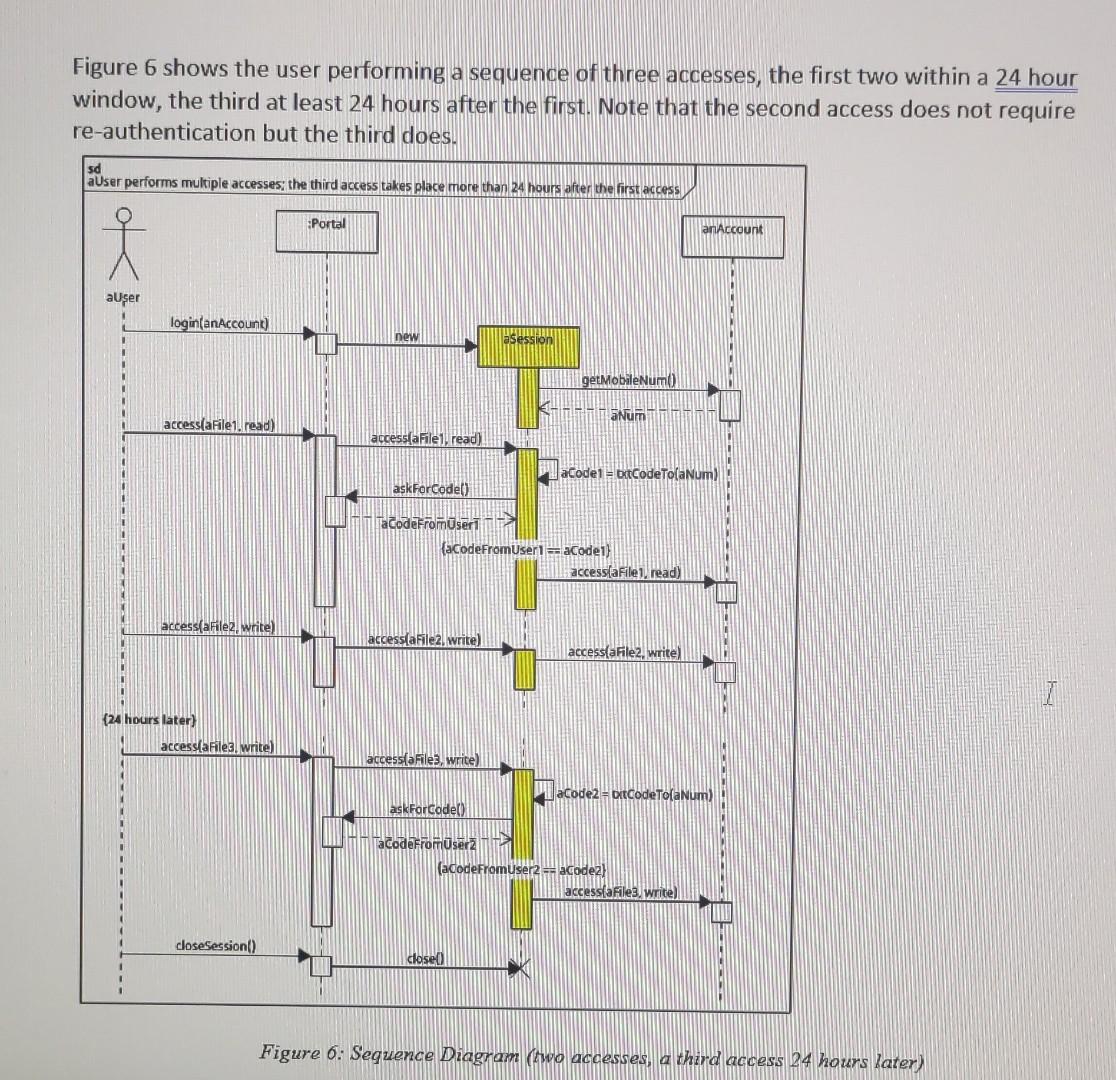
Figure 6 shows the user performing a sequence of three accesses, the first two within a 24 hour window, the third at least 24 hours after the first. Note that the second access does not require re (1) ] Figure 6: Sequence Diagram (wo accesses, a third access 24 hours later)
Design task Design the inner workings of the Session class by developing a state machine diagram. Determine what states a Session instance goes through, what events trigger state changes, and what activities the Session instance performs. Pay attention to details. Your state machine diagram must use the correct UML syntax and be coherent with the class diagram and the sequence diagrams. You may have to add new attributes to the session class in order to design your state machine.
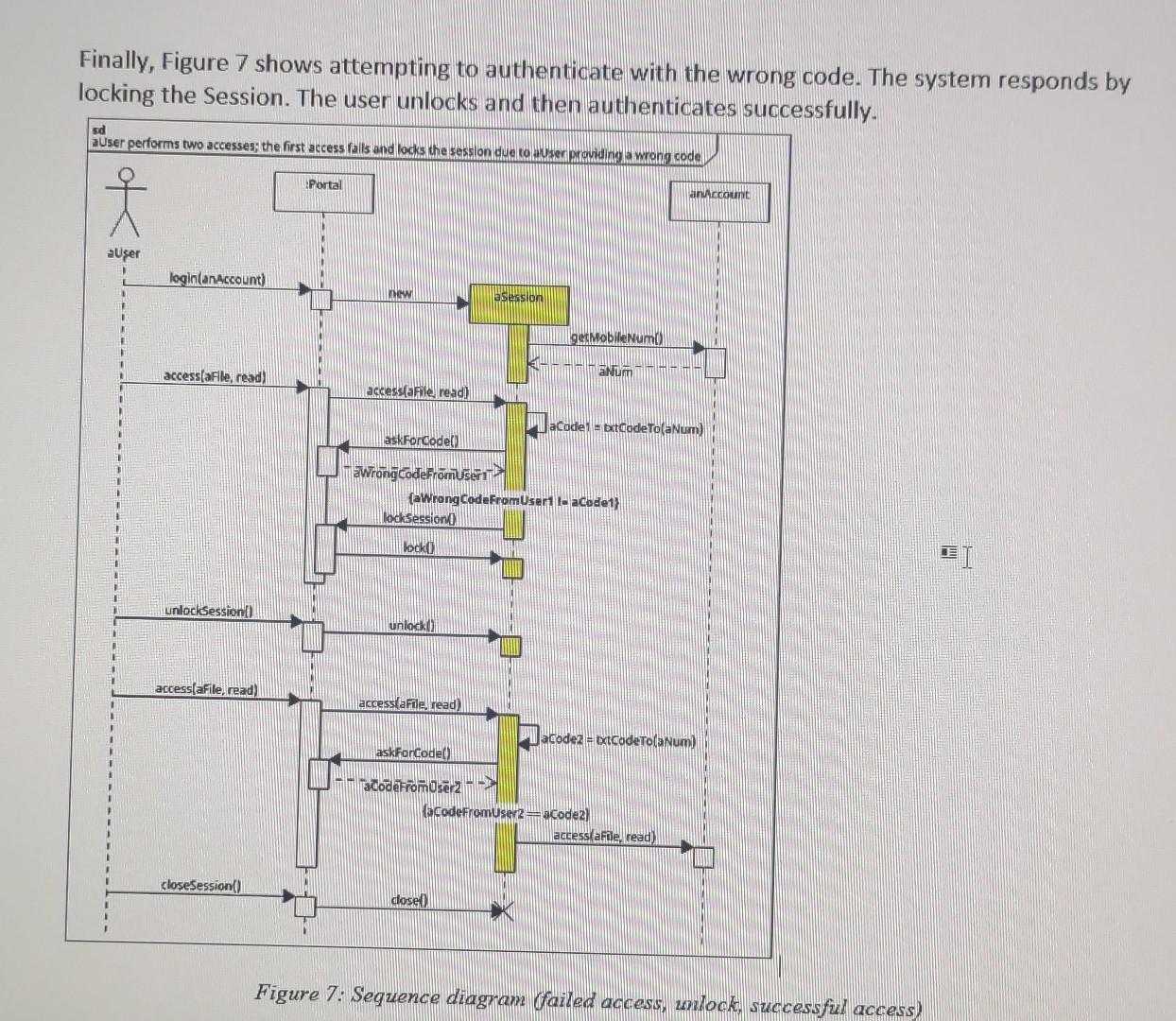
Finally, Figure 7 shows attempting to authenticate with the wrong code. The system responds by locking the Session. The user unlocks and then authenticates successfully. Figure 7: Sequence diagnam (failed access, wilock, successful access)